Fortinet Acquires Next DLP Strengthens its Top-Tier Unified SASE Solution
Read the release

The growing reliance on cloud applications and the widespread use of personal devices for work have revolutionized the modern workplace. As organizations increasingly adopt cloud-based solutions to enhance flexibility and collaboration, employees are leveraging their personal devices to access corporate resources from anywhere. This shift towards a more mobile and decentralized workforce offers numerous benefits, including increased productivity and operational efficiency. However, it also introduces new security challenges, as sensitive data becomes more dispersed and vulnerable to sophisticated cyber threats. The average cost of a breach — $4.45m — underscores the significance of data protection for modern enterprises in the Cloud and Mobile era.
To address these challenges, Next DLP introduces Reveal Beyond, an advanced cybersecurity solution designed to safeguard modern, cloud-centric environments while ensuring robust protection across both corporate and personal devices.

|
It’s reported that 87% of employees are accessing company data through their personal device. But did you know that 50% of companies that allowed this experienced a data breach via said device? Based upon our own analysis of data from the Reveal Platform, to better understand the mechanisms through which sensitive data is leaked out of corporate networks, we observed that “Insiders transferring data to personal online storage accounts for over 17% of detected exfiltration activities”.
Traditional data security solutions, such as Endpoint Data Loss Prevention, Firewall or Network Data Loss Prevention, Email Data Loss Prevention, Cloud Access Security Broker and Reverse Proxy approaches can protect against some but not all exfiltration methods. Additionally, traditional solutions often operate in silos, lacking the integration and context needed to provide comprehensive protection.
Employees with access to Cloud apps from their personal endpoints may accidentally copy, paste, or upload sensitive data. For instance, sales employees might use their personal mobile device to draft emails, marketing teams could generate content, and developers might create code, all utilizing sensitive data downloaded from or uploaded to an approved Cloud application.
Adversaries with access to valid credentials and malicious insiders with access to sensitive data stores pose significant risks to organizational security, particularly through personal mobile devices. These threats exploit the convenience and connectivity of mobile devices to facilitate data leakage, often bypassing traditional security measures. Adversaries can use stolen credentials to gain unauthorized access to critical systems and sensitive information, while malicious insiders can intentionally exfiltrate data using their legitimate access privileges.
Whether it’s accidental or malicious, the potential consequences are catastrophic: damage to brand reputation, compliance fines and loss of intellectual property. Addressing these vulnerabilities requires a comprehensive approach that includes stringent access controls, continuous monitoring, and advanced threat detection capabilities to mitigate the risk of data leakage through personal mobile devices.
Reveal is a data security platform that addresses Data Loss Prevention (DLP), Insider Risk Management (IRM), and Cloud Data Security use cases. Reveal provides organizations with a unified data security platform offering comprehensive user and data event visibility, content and context aware sensitive data identification, risk-adaptive data protection control and user behavioral analytics across managed and unmanaged devices.
Reveal Beyond, a capability of the Reveal platform, takes a modern approach to securing your enterprise data from adversaries. Reveal Beyond delivers data protection across the Cloud, Managed, and Unmanaged Devices and surfaces the much-needed context to content, automatically connecting the dots across who, what, how, why and where of your data, no matter what the device, in a single console. This capability, which empowers enterprises to prevent data theft in the Cloud and Mobile era, is missing from legacy DLP solutions.
Let’s assume organizations have governance frameworks with periodic user training on personal device usage. These are important and nice to have, but they don’t stop those devices being an exfiltration vector. Reveal Beyond empowers organizations with the “must-haves” for safer Cloud app and Mobile device usage:
Reveal provides robust data loss prevention, insider risk management, and cloud data security capabilities that extend across both managed and unmanaged devices. This section delves into critical use cases where Reveal Beyond excels, such as SaaS visibility and detection of exfiltration activities from unmanaged devices. By exploring scenarios like an employee using a combination of managed and unmanaged devices to steal company IP, we highlight how Reveal Beyond's comprehensive visibility and protection mechanisms can prevent data breaches. Additionally, we examine the platform's ability to monitor and control data transfers to unmanaged devices, ensuring that even personal devices are within the security perimeter. Through proactive policy enforcement and interactive employee notifications, Reveal Beyond not only detects but also mitigates risks, making it an essential tool for modern data security.
|
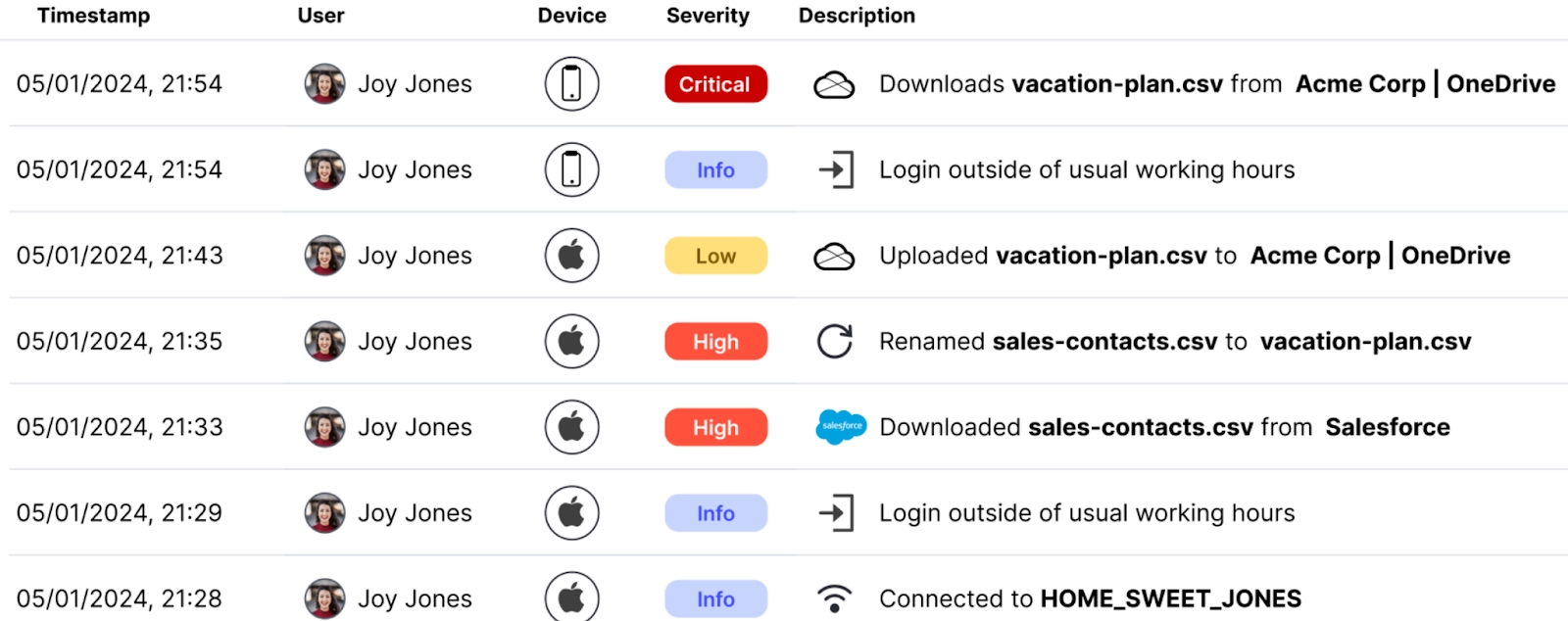
As a unified data protection solution, Reveal gives you data loss prevention, insider risk management and cloud data security capabilities, across both managed and unmanaged devices. In this very common exfiltration sequence an employee looking to steal company IP is using a mix of managed and unmanaged devices and cloud applications to exfiltrate data.
This sequence started with Joy using her managed work machine from her home office. She logged in outside of usual working hours, nothing too concerning there. Then she downloaded a contacts file from Salesforce. OK, maybe she needs to do some spreadsheet analysis that’s not possible in the cloud app?
Joy then renamed the file to vacation-plans. Does Joy think that this is a way to bypass security controls and visibility? Things are starting to get suspicious! Next, Joy uploaded the renamed file to a cloud drive. Then, the smoking gun! Joy downloaded the file to her personal mobile device, exfiltrating data and violating company policy.
|
How often are your employees working on their personal unmanaged devices? And when they need to complete a task, how often do you think they are bypassing company controls and policy, for example, exporting a file from the cloud to a local PDF or emailing a file to their personal address?
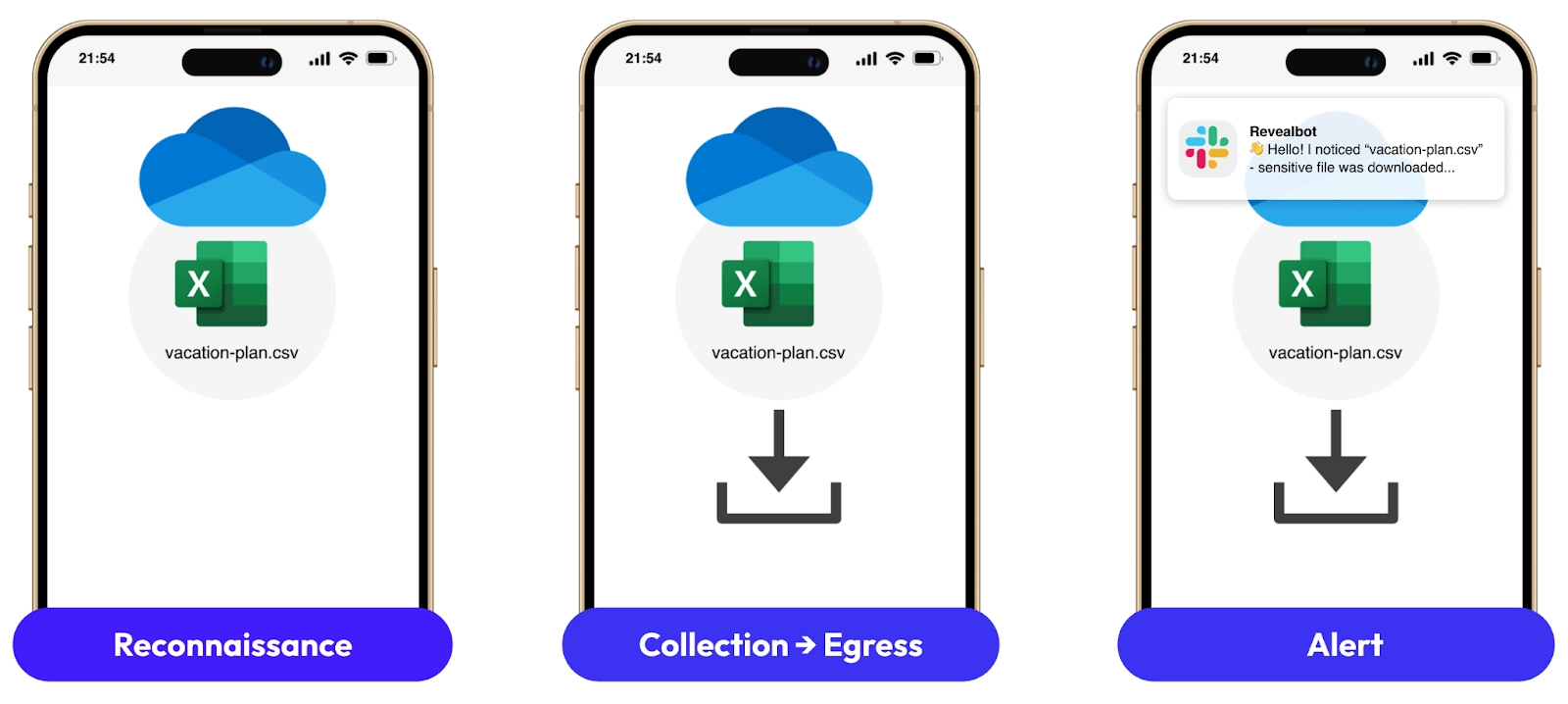
Reveal sees sanctioned cloud app activity, even when the user is on their personal unmanaged device. From Reconnaissance, where it sees what folder the user is accessing, annotating origin information if the user creates a copy of the file, to ultimately seeing exfiltration to the mobile device. Policy can be used to block user access at this point, or we can make the employee part of the solution.
Just like we are used to receiving an alert from our bank on suspicious activity, the Reveal APIs can be used to send an interactive notification to your messaging app, for example Slack. The message to the employee will let them know what Reveal is seeing, and the interactive interface gives the employee an opportunity to respond. Oftentimes, this notification is enough to correct employee behavior.
The modern workplace's reliance on cloud applications and personal devices has revolutionized productivity and collaboration, but it also brings significant security challenges. With employees accessing corporate resources from various locations and devices, sensitive data becomes more dispersed and vulnerable to sophisticated threats. The high average cost of a data breach, around $4.45 million, highlights the critical need for robust data protection measures in this Cloud and Mobile era.
Reveal Beyond addresses these challenges head-on, offering a comprehensive data security solution that integrates data loss prevention, insider risk management, and cloud data security. Reveal Beyond excels in providing visibility and protection across managed and unmanaged devices, ensuring that even personal devices fall within the security perimeter. By leveraging advanced capabilities such as real-time data monitoring, granular classification, and proactive policy enforcement, Reveal Beyond empowers organizations to detect and mitigate risks effectively.
Incorporating Reveal into your cybersecurity strategy means embracing a unified approach to data security that combines advanced technologies and contextual intelligence. Reveal not only protects against data breaches but also educates and involves employees in maintaining data integrity. As organizations continue to navigate the complexities of the digital age, Reveal stands out as an essential tool for safeguarding sensitive information and ensuring a secure, compliant, and resilient business environment.

Blog

Blog

Blog

Blog

Resources

Resources

Resources

Resources
